Security issues and countermeasures in digitalization to achieve DX
Information and communication networks in the digital age
Ensuring safety and reliability
In recent years, digitalization has progressed significantly, with the promotion of digital transformation (DX) and the automation of business processes to alleviate labor shortages. As digitalization becomes a part of people's lives, security measures are becoming even more important.
The following statement is also included in the ICT Cybersecurity Comprehensive Measures 2022, published by the Ministry of Internal Affairs and Communications in August 2022:
"As cyberspace becomes a public space used by all entities, information and communications networks that support digitalization have become an important and indispensable foundation for people's lives and economic activities, and their importance is increasing even further.
(Omitted)
Under these circumstances, it is becoming increasingly important to ensure the safety and reliability of information and communications networks.
In addition, the revised Personal Information Protection Act also makes it possible to request disclosure of traceability records, including when and to whom the data was provided and from whom it was received, when personal information is provided to a third party.
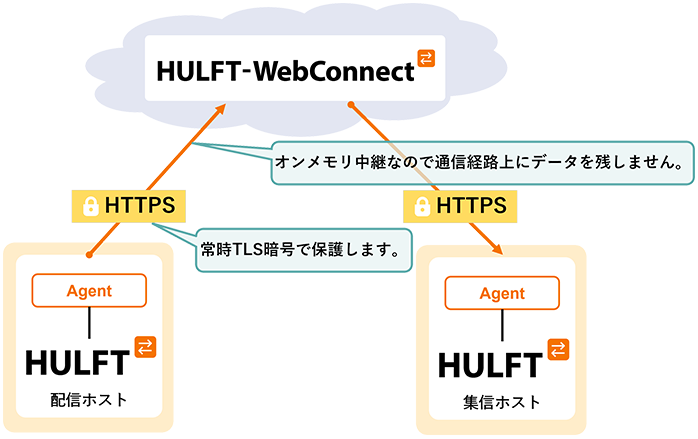
Countermeasure 1: Encryption of communication routes
Encrypting communication channels makes it possible to prevent data eavesdropping, spoofing, and tampering.
Protect your information assets by blocking attack routes from outside the company.
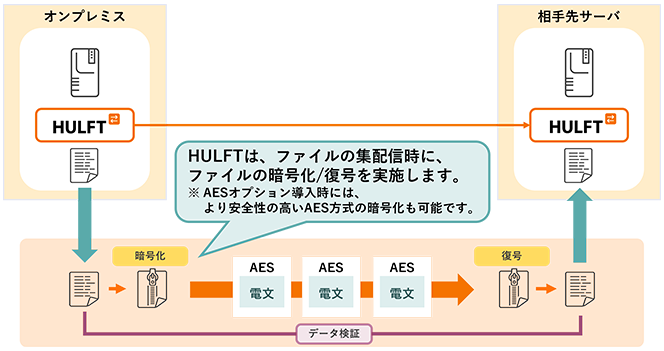
Countermeasure 2: Data encryption
Data encryption can prevent damage from spreading if data is leaked, and also prevents data from being misused if it is stolen.
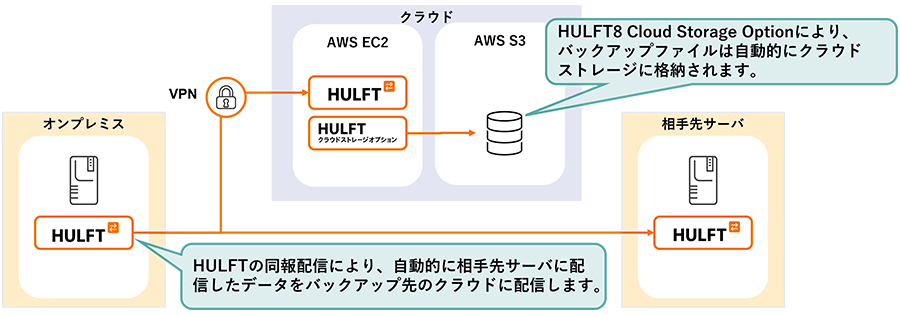
Countermeasure 3: Back up your data
Data backups enhance business continuity by allowing recovery from backup data in the event of data corruption, data freezing due to ransomware attacks, and even in the event of server damage due to natural disasters.
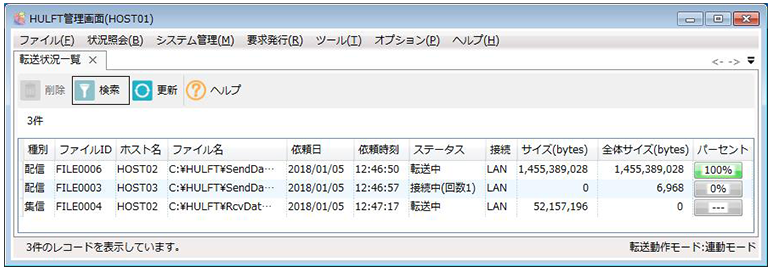
Countermeasure 4: Log management
Log management ensures traceability in the event of a security incident.
Being able to see when and where data was sent allows for quicker response.